This is a leading topic nowadays, Security in an application has become the most worrisome subject of our modern days. The privacy of users is normally compromised when Developers or any person responsible for security leave room for unwanted access.
Security should be among the first priorities to consider and implement, there are many factors leading to a lack of Security, and unwanted access to prohibited resources is normally performed by enthusiast Analysts, therefore, Developers should be up to par about security issues. One way to archive this is by ( patching ) updating the Server/Operating System more often and paying attention to requests that come into your Server.
If, you want to take this to another level, then look into various Data Encryption Algorithms. Although, security is not guaranteed 100 percent, however, it can be partially eradicated when done right.
Developers together as a team should be aware of new threats and know how to protect the user, ways to make sure that the application is secure start with the Stuff that is not even involved in Software Development Life Cycle. Why should the Staff working around the application be trained on security threats? You ask.
The most vulnerable way to exploit an application would be to exploit people who have access to secure applications. For example, someone would play a YouTube Video with the sound of a baby crying and pretend to be one of the users and request a password change.
Due to the nature of the call, someone might believe the call is from a legit user and hand over sensitive account information. In order to better prepare, below is a list of some things that need to be thought about for security purposes.
- Make sure that no sensitive information is exposed through JavaScript, this applies to Application Programming Interfaces (API). A very common mistake is when a Developer codes an API endpoint and Authorization Keys right into JavaScript. The important thing to remember is that JavaScript gets transferred or transported through HTTP, which means it runs on the Browser side.
Anything that runs on the Browser (Front-End) gets exposed. One way to see what JavaScript and HTML along with CSS files come with the website you visited is by going to the Browser Options tab where the “More Tools” option tab can be found and navigating to the Developer’s Tools, in the Developers section there are several tools but one of them, in particular, is “Network”. Below is a picture to illustrate this point.
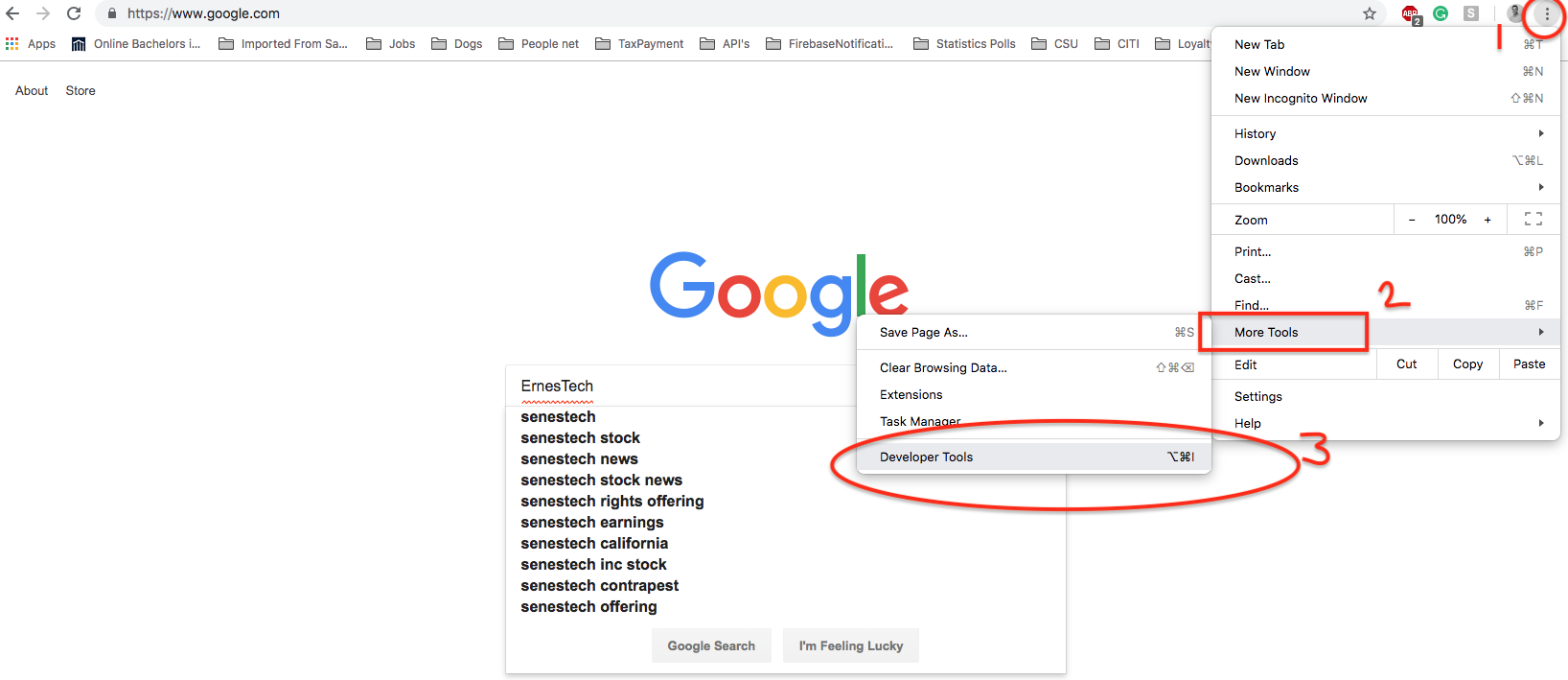
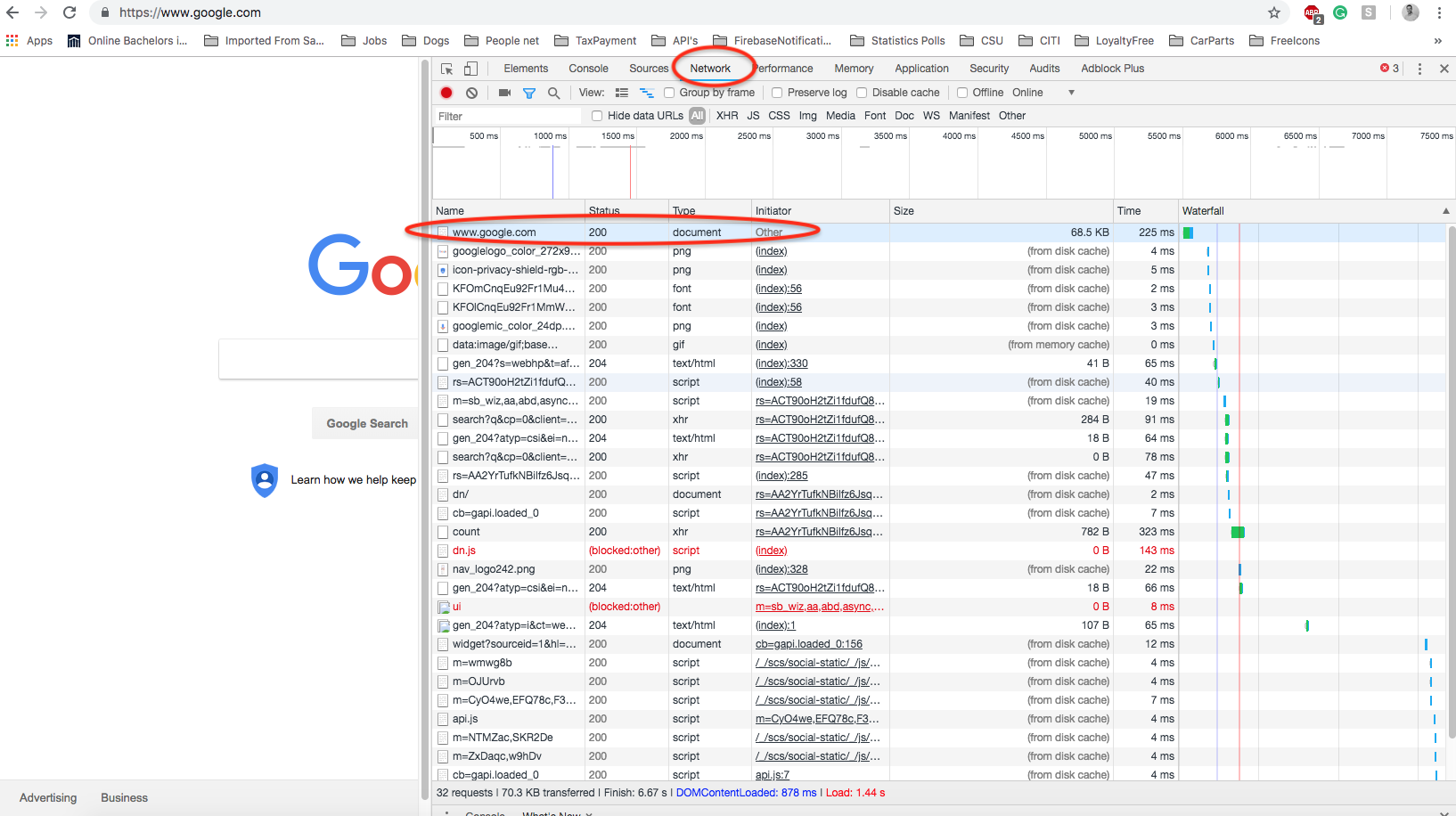
JavaScript is not going away anytime soon, it has its own pros and cons and when it comes to Security it is important to be aware of how Hackers can exploit the application to better protect users’ data.
- Use a strong layer of Authentication, if you decide to implement this layer of security by yourself just know that there are challenges and this is the most important door to your application. If this layer is exploited, there will be flaws in the application.
Choosing a well-maintained and secure library is vital to data security. In this book, we will be using Microsoft’s Membership Library, although there are many Authentication Libraries provided by companies like Google, Facebook, and many third-party authentication API, Membership Library comes ready with the Boilerplate template that we will be using to make our application.
- Separate what files or information different users can access by utilizing a file in the application we will be making called Web.config. This file (Web.config) allows whether all users can access certain folders or only authenticated users can. This is very important to make sure only certain users
- Minimize the use of third-party libraries, although it is nearly impossible to develop an application entirely by using your tools, Software Developers rely on third-party tools like IDE (Integrated Development Environment), a software used to make software or applications.
In addition, libraries are likely to be precompiled classes called Dynamic Link-Library (DLL) in C-Sharp or Jar files in Java which means you do not have full access to see the source code or change code to suit your needs.
Third-party libraries are called APIs because the owner has coded the classes and hosted them on Servers so other Developers can access them. There is no need to reinvent the wheel when it comes to developing a Social Media application, however, Developers should strive to make their own libraries to reduce dependencies.
- According to Sans Technology Institutes, Physical Security can result in more damage than a virus called a “Worm” (Security Laboratory). Physical Security is the most vulnerable form of exploit when it comes to protecting users’ data or intellectual Property. Imagine someone calling your office pretending to be a user of your application and requesting a password to be changed or just asking about sensitive information.
If employees are not well trained, they might think that by providing information they are serving the customer. In lieu of this point, the Data Center (no matter how small it might be) should be protected by making sure that the location is well-secured and operated by authorized employees.
- Choose Secure Hosting that doesn’t allow files to be viewed, it is important to do virtual research about the hosting Company the application will be hosted. Latest programming Frameworks like .Net Core now allow the application to be hosted on a Linux-like Operating System.
This has brought change to compatibility and a flexible hosting environment. However, in order for an application to meet its optimal performance, the hosting environment needs to be assessed for further requirements.
Hosting is a huge factor in an application's success, you should always look at how reliable the Hosting Company is and ask questions like; what is the downtime, how often does the hosting company maintain their servers, and how big is their Internet bandwidth (1000 Megabits per Second or 60 Mbps), do they use Fiber Optic Cables, what is their track record, have they been hacked in the past, and whether or not the hosting Company has other location around the World.
This is very important because you do not want your application to be hosted on another region’s server and serve the user from another part of the World. Find out if the Hosting Company offers Content Delivery Network (CDN) that makes sure that your application is hosted close to the location where users are.

